Description:-
- DBSAT is lightweight, easy to run and deploy and quickly provides a view on the database security configuration, the database users, their entitlements, security policies, security controls, and where sensitive data resides.
- The Oracle Database Security Assessment Tool (DBSAT) is a stand-alone command line tool that accelerates the assessment and regulatory compliance process by collecting relevant types of configuration information from the database and evaluating the current security state to provide recommendations on how to mitigate the identified risks.
- You can use DBSAT to implement and enforce security best practices in your organization. DBSAT reports on the state of user accounts, role and privilege grants, and policies that control the use of various security features in the database.
- Oracle released the version 2.0.2 (May 2018) Database Security Assessment Tool (DBSAT)
Summary: Oracle DBSAT
• Quickly assess the current security status of database before hackers do
• Identify sensitive data to determine risk and appropriate security controls
• Reduce risk exposure using proven best practices
• Accelerate compliance with EU GDPR and other regulations
• Support Oracle Database 10g, 11g, 12c and 18c
• Provided at no additional cost to Oracle customers
- Database Security Assessment Tool Components
Collector:- The Collector executes SQL queries and runs operating system commands to collect data from the system to be assessed. It does this primarily by querying database dictionary views. The collected data is written to a JSON file that is used by the DBSAT Reporter in the analysis phase. Reporter:- The Reporter analyzes the collected data and generates a Database Security Assessment Report in HTML, Excel, JSON, and Text formats. The Reporter can run on any machine: PC, laptop, or server. You are not limited to running the Reporter on the database server or the same machine as the Collector. Discoverer:- The Discoverer executes SQL queries and collects data from the system to be assessed, based on the settings specified in the configuration files. It does this primarily by querying database dictionary views. The collected data is then used to generate a Database Sensitive Data Assessment Report in HTML and CSV formats. The Discoverer can run on any machine: PC, laptop, or server. You are not limited to running the Discoverer on the database server or the same machine as the Collector or Reporter.
Prerequisites
Supported Operating Systems
DBSAT runs on:
Solaris x64 and Solaris SPARC64
Linux x86-64
Windows x64
HP-UX IA (64-bit)
IBM AIX (64-bit) & Linux on zSeries (64-bit)
Supported Database Versions
Support Oracle Database 10g(10.2.0.5), 11g, 12c and 18c
Security Requirements
DBSAT output files are sensitive because they may reveal weaknesses in the security posture of your database. To prevent unauthorized access to these files, you must implement the following security guidelines:
- Ensure that the directories holding these files are secured with the appropriate permissions.
- Delete the files securely after you implement the recommendations they contain.
- Share them with others in their (by default) encrypted form.
- Grant user permissions on a short-term basis and revoke these when no longer necessary.
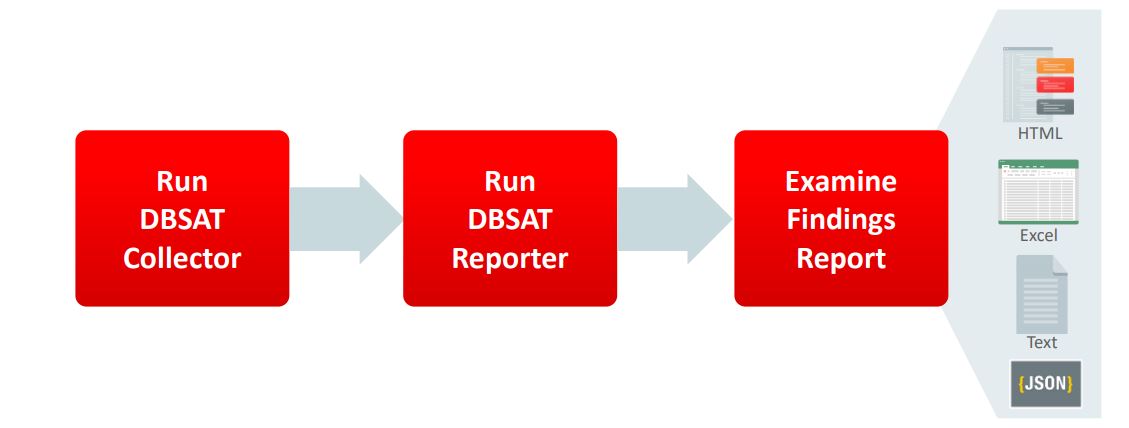
Let’s Start the demo
Download the DBSTAT TOOL Here
Installing the Database Security Assessment Tool
Step1:-Log in to the database server.
Step2:-Create the dbsat directory:
mkdir –p /home/oracle/dbsat
Step3:-Download or copy the dbsat.zip file to the database server, and unzip the file.
unzip dbsat.zip –d /home/oracle/dbsat
Where -d refers to the directory path.
[oracle@primary u01]$ unzip dbsat.zip -d /home/oracle/dbsat Archive: dbsat.zip inflating: /home/oracle/dbsat/dbsat inflating: /home/oracle/dbsat/dbsat.bat inflating: /home/oracle/dbsat/sat_reporter.py inflating: /home/oracle/dbsat/sat_analysis.py inflating: /home/oracle/dbsat/sat_collector.sql inflating: /home/oracle/dbsat/xlsxwriter/app.py inflating: /home/oracle/dbsat/xlsxwriter/chart_area.py inflating: /home/oracle/dbsat/xlsxwriter/chart_bar.py inflating: /home/oracle/dbsat/xlsxwriter/chart_column.py inflating: /home/oracle/dbsat/xlsxwriter/chart_doughnut.py inflating: /home/oracle/dbsat/xlsxwriter/chart_line.py inflating: /home/oracle/dbsat/xlsxwriter/chart_pie.py inflating: /home/oracle/dbsat/xlsxwriter/chart.py inflating: /home/oracle/dbsat/xlsxwriter/chart_radar.py inflating: /home/oracle/dbsat/xlsxwriter/chart_scatter.py inflating: /home/oracle/dbsat/xlsxwriter/chartsheet.py inflating: /home/oracle/dbsat/xlsxwriter/chart_stock.py inflating: /home/oracle/dbsat/xlsxwriter/comments.py inflating: /home/oracle/dbsat/xlsxwriter/compat_collections.py inflating: /home/oracle/dbsat/xlsxwriter/compatibility.py inflating: /home/oracle/dbsat/xlsxwriter/contenttypes.py inflating: /home/oracle/dbsat/xlsxwriter/core.py inflating: /home/oracle/dbsat/xlsxwriter/custom.py inflating: /home/oracle/dbsat/xlsxwriter/drawing.py inflating: /home/oracle/dbsat/xlsxwriter/format.py inflating: /home/oracle/dbsat/xlsxwriter/__init__.py inflating: /home/oracle/dbsat/xlsxwriter/packager.py inflating: /home/oracle/dbsat/xlsxwriter/relationships.py inflating: /home/oracle/dbsat/xlsxwriter/shape.py inflating: /home/oracle/dbsat/xlsxwriter/sharedstrings.py inflating: /home/oracle/dbsat/xlsxwriter/styles.py inflating: /home/oracle/dbsat/xlsxwriter/table.py inflating: /home/oracle/dbsat/xlsxwriter/theme.py inflating: /home/oracle/dbsat/xlsxwriter/utility.py inflating: /home/oracle/dbsat/xlsxwriter/vml.py inflating: /home/oracle/dbsat/xlsxwriter/workbook.py inflating: /home/oracle/dbsat/xlsxwriter/worksheet.py inflating: /home/oracle/dbsat/xlsxwriter/xmlwriter.py inflating: /home/oracle/dbsat/xlsxwriter/LICENSE.txt inflating: /home/oracle/dbsat/Discover/bin/discoverer.jar inflating: /home/oracle/dbsat/Discover/lib/ojdbc8.jar inflating: /home/oracle/dbsat/Discover/lib/oraclepki.jar inflating: /home/oracle/dbsat/Discover/lib/osdt_cert.jar inflating: /home/oracle/dbsat/Discover/lib/osdt_core.jar inflating: /home/oracle/dbsat/Discover/conf/sample_dbsat.config inflating: /home/oracle/dbsat/Discover/conf/sensitive_en.ini
Using the Database Security Assessment Tool
You can generate the following reports with the Collector, Reporter, and Discoverer components:
Database Security Assessment Report
The Collector and Reporter components are used to generate a Database Security Assessment Report.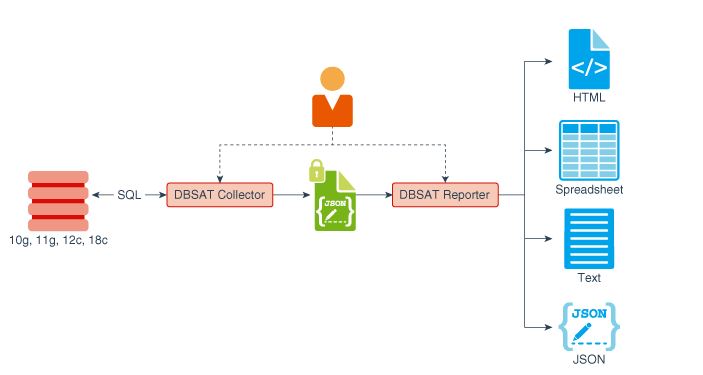
Running the Collector
The Collector connects to the database.
Ensure that the target database and listener are running before running the Collector.
Step1:-Specify the arguments to run the Collector:
$ dbsat collect <connect_string> <destination>
The dbsat collect command has the following options and arguments:
connect_string
Specifies the connection string to connect to the database.
Example: dbsat@orcl
destination
Specifies the location and file name for the Database Security Assessment report.
Example: /home/oracle/dbsat/db04
Step2:-Run the Collector.
$ ./dbsat collect dbsat@orcl db04
cd /home/oracle/dbsat/
[oracle@primary dbsat]$ ./dbsat collect system@prime /u01/statreport
Database Security Assessment Tool version 2.0.2 (May 2018)
This tool is intended to assist in you in securing your Oracle database
system. You are solely responsible for your system and the effect and
results of the execution of this tool (including, without limitation,
any damage or data loss). Further, the output generated by this tool may
include potentially sensitive system configuration data and information
that could be used by a skilled attacker to penetrate your system. You
are solely responsible for ensuring that the output of this tool,
including any generated reports, is handled in accordance with your
company's policies.
Connecting to the target Oracle database...
SQL*Plus: Release 12.1.0.2.0 Production on Thu Jul 5 00:05:08 2018
Copyright (c) 1982, 2014, Oracle. All rights reserved.
Enter password:
Last Successful login time: Wed Jun 20 2018 23:51:14 +05:30
Connected to:
Oracle Database 12c Enterprise Edition Release 12.1.0.2.0 - 64bit Production
With the Partitioning, OLAP, Advanced Analytics and Real Application Testing options
Setup complete.
SQL queries complete.
OS commands complete.
Disconnected from Oracle Database 12c Enterprise Edition Release 12.1.0.2.0 - 64bit Production
With the Partitioning, OLAP, Advanced Analytics and Real Application Testing options
DBSAT Collector completed successfully.
Calling /u01/app/oracle/product/12.1.0.2/db_1/bin/zip to encrypt statreport.json...
Enter password:
Verify password:
adding: statreport.json (deflated 86%)
zip completed successfully.
Running the Reporter
Note :-Python Version needs upgrade
Download Here & Steps to install Python Here
The Reporter analyses the data collected by the Collector and makes recommendations to improve the security of the database.
Step1:-You can invoke the Reporter with dbsat report.
To run the Reporter, do the following:
Check that Python version is 2.6 or later is installed.
[oracle@db04 sat]$ python -V
A similar output is displayed:
Python 2.7.11rc1
Specify the arguments to run the Reporter. $ dbsat report [-a] [-n] [-x <section>] <pathname> Where the argument pathname stands for the full or relative path name to the data file db04 produced by the DBSAT Collector. If this file was encrypted during data collection, you will need to supply the encryption password when prompted by the Reporter. The Reporter supports the following command-line options: -a means: include all the database user accounts in the analysis. (Locked Oracle-supplied accounts are excluded by default as they cannot be used to connect to the database.) -n means: do not encrypt the reports generated by the analysis. -x means: exclude a section from the report. Valid sections are: USER : User Accounts PRIV : Privileges and Roles AUTH : Authorization Control CRYPT : Data Encryption ACCESS :Fine-Grained Access Control AUDIT : Auditing CONF : Database Configuration NET : Network Configuration OS : Operating System To exclude multiple sections use a comma-separated list, for example: -x USER,PRIV Or: —x USER —x PRIV Omitting this option will include all sections of the report. The same path name is used to generate the report files produced by the Reporter in HTML, Excel, JSON, and Text formats with the appropriate file extensions.
Step2:-Run the Reporter.
$ ./dbsat report /u01/statreport
[oracle@primary ~]$ /usr/local/bin/python2.7 -V Python 2.7.15 [oracle@primary dbsat]$ ./dbsat report /u01/statreport Database Security Assessment Tool version 2.0.2 (May 2018) This tool is intended to assist in you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies. Archive: statreport.zip [statreport.zip] statreport.json password: inflating: statreport.json DBSAT Reporter ran successfully. Calling /usr/bin/zip to encrypt the generated reports... Enter password: Verify password: zip warning: statreport_report.zip not found or empty adding: statreport_report.txt (deflated 78%) adding: statreport_report.html (deflated 84%) adding: statreport_report.xlsx (deflated 3%) adding: statreport_report.json (deflated 82%) zip completed successfully.
Running the Discoverer
Note:-Java version 1.8 or later is required
export JAVA_HOME=/usr/java/jdk1.8.0_171-amd64 [oracle@primary dbsat]$ ./dbsat discover -c Discover/conf/dbsat.config prime Database Security Assessment Tool version 2.0.2 (May 2018) This tool is intended to assist in you in securing your Oracle database system. You are solely responsible for your system and the effect and results of the execution of this tool (including, without limitation, any damage or data loss). Further, the output generated by this tool may include potentially sensitive system configuration data and information that could be used by a skilled attacker to penetrate your system. You are solely responsible for ensuring that the output of this tool, including any generated reports, is handled in accordance with your company's policies. Enter username: system Enter password: DBSAT Discover ran successfully. Calling /usr/bin/zip to encrypt the generated reports... Enter password: Verify password: zip warning: prime_report.zip not found or empty adding: prime_discover.html (deflated 84%) adding: prime_discover.csv (deflated 82%) Zip completed successfully.
Unzip the Report
[oracle@primary dbsat]$ ls -lrt total 400 -r-xr-xr-x. 1 oracle oinstall 28216 Dec 21 2017 sat_analysis.py -r-xr-xr-x. 1 oracle oinstall 248371 Apr 13 05:03 sat_reporter.py -r-xr-xr-x. 1 oracle oinstall 12839 May 1 20:07 dbsat -r-xr-xr-x. 1 oracle oinstall 12771 May 18 12:32 dbsat.bat -r-xr-xr-x. 1 oracle oinstall 43796 May 31 14:53 sat_collector.sql drwxr-xr-x. 5 oracle oinstall 4096 Jul 4 23:49 Discover -r--------. 1 oracle oinstall 25095 Jul 5 00:34 sat_analysis.pyc drwxr-xr-x. 2 oracle oinstall 4096 Jul 5 00:34 xlsxwriter -rw-------. 1 oracle oinstall 68 Jul 5 01:27 discoverer.log -rw-------. 1 oracle oinstall 9330 Jul 5 01:28 prime_report.zip [oracle@primary dbsat]$ unzip prime_report.zip Archive: prime_report.zip [prime_report.zip] prime_discover.html password: inflating: prime_discover.html inflating: prime_discover.csv [oracle@primary dbsat]$ ls -lrt total 460 -r-xr-xr-x. 1 oracle oinstall 28216 Dec 21 2017 sat_analysis.py -r-xr-xr-x. 1 oracle oinstall 248371 Apr 13 05:03 sat_reporter.py -r-xr-xr-x. 1 oracle oinstall 12839 May 1 20:07 dbsat -r-xr-xr-x. 1 oracle oinstall 12771 May 18 12:32 dbsat.bat -r-xr-xr-x. 1 oracle oinstall 43796 May 31 14:53 sat_collector.sql drwxr-xr-x. 5 oracle oinstall 4096 Jul 4 23:49 Discover -r--------. 1 oracle oinstall 25095 Jul 5 00:34 sat_analysis.pyc drwxr-xr-x. 2 oracle oinstall 4096 Jul 5 00:34 xlsxwriter -rw-------. 1 oracle oinstall 68 Jul 5 01:27 discoverer.log -rw-------. 1 oracle oinstall 41026 Jul 5 01:28 prime_discover.html -rw-------. 1 oracle oinstall 13076 Jul 5 01:28 prime_discover.csv -rw-------. 1 oracle oinstall 9330 Jul 5 01:28 prime_report.zip
Sample Report Here
Reference:-
https://docs.oracle.com/cd/E93129_01/SATUG/toc.htm#SATUG-GUID-999F5696-F368-4E54-86DB-DEFC593B2042
Catch Me On:- Hariprasath Rajaram
LinkedIn:https://www.linkedin.com/in/hari-prasath-aa65bb19/
Facebook:https://www.facebook.com/HariPrasathdba
FB Group:https://www.facebook.com/groups/894402327369506/
FB Page: https://www.facebook.com/dbahariprasath/?
Twitter: https://twitter.com/hariprasathdba